This leads them to arrest criminals and enable them to be convicted in court. Know how youll tell people if theres a security breach so they can protect themselves from potential identity theft.
Forensic tools techniques and procedures conducted aid auditors in detecting abnormalities such as misstatement of financial facts prevention and detection of fraud.
. It also provides relevant updates news and historical events connected to IRS CI. Credit card fraud is an inclusive term for fraud committed using a payment card such as a credit card or debit card. Database forensics can be defined as the application of computer investigation and the analysis techniques to gather the evidences from the database to present them in a court of law.
The purpose may be to obtain goods or services or to make payment to another account which is controlled by a criminal. This page provides career information about the Internal Revenue Service IRS Criminal Investigation CI Special Agent position. This includes critical peace officer jailer 911 telecommunications and security e-commerce training.
Forensic audit techniques tools and procedures are used to identify and. Getting educated and taking a few basic steps may keep you from becoming a victim of crime and fraud. Upon completion of the investigation if it is found that you were a true victim of identity theft a revised 1099G will be issued to you.
The Payment Card Industry Data Security Standard PCI DSS is the data security standard created to help financial institutions process. Or 2 the object of the call is to receive help in a. OSS Academy provides quality online law enforcement corrections and telecommunications training courses.
Lateral movement attacks are typically accomplished using a number of different techniques. In both methods your non-sensitive accounts are used by attackers for lateral moves by exploiting non-sensitive machines that share stored log-in credentials in accounts groups. Some of the most popular methods used by attackers are credential theft and Pass the Ticket.
A forensic investigation needs to be done on the databases because a database has sensitive data where there is a high chance of a security breach by the intruders to get this. 1 the agency determines that revealing the identity may threaten the personal safety or property of any person. This site offers hiring tips information about what it is like to be an 1811 special agent.
Our adult based learning programs are interactive and are in use by numerous professional public safety entities. Contacting one of the three credit bureaus to place a fraud alert on their account. The department uses a variety of techniques to uncover fraud.
Share IRS Publication 5027 Identity Theft Information for Taxpayers PDF with employees and direct them to the Steps for Identity Theft Victims which includes. Identity Theft Insurance Restoration Services. A detective may work for the police or privately.
Identity theft is a serious crime that occurs when someone else uses your personally identifiable information such as your name. The identity theft insurance benefit for members is underwritten and administered by any one of the following insurance carriers depending upon your program. AIG Assurant or Hamilton Insurance DAC andor its affiliates.
Identity theft and identity fraud are terms used to refer to all types of crime in which someone wrongfully obtains and uses another persons personal data in some way that involves fraud or deception typically for economic gain. They may consider placing a credit freeze which offers more protection. A detective is an investigator usually a member of a law enforcement agencyThey often collect information to solve crimes by talking to witnesses and informants collecting physical evidence or searching records in databases.
We source expert presenters for our webinars and secure pre-approval for continuing professional education CPE credit with the Human Resources Certification Institute HRCI and other certifying bodies when appropriate. You must also show how you meet these rules in. F when access to the data would reveal the identity of a person who placed a call to a 911 system or the identity or telephone number of a service subscriber whose phone is used to place a call to the 911 system and.

Tips And Advice To Prevent Identity Theft Happening To You Europol

Cyber Crime Investigation Making A Safer Internet Space
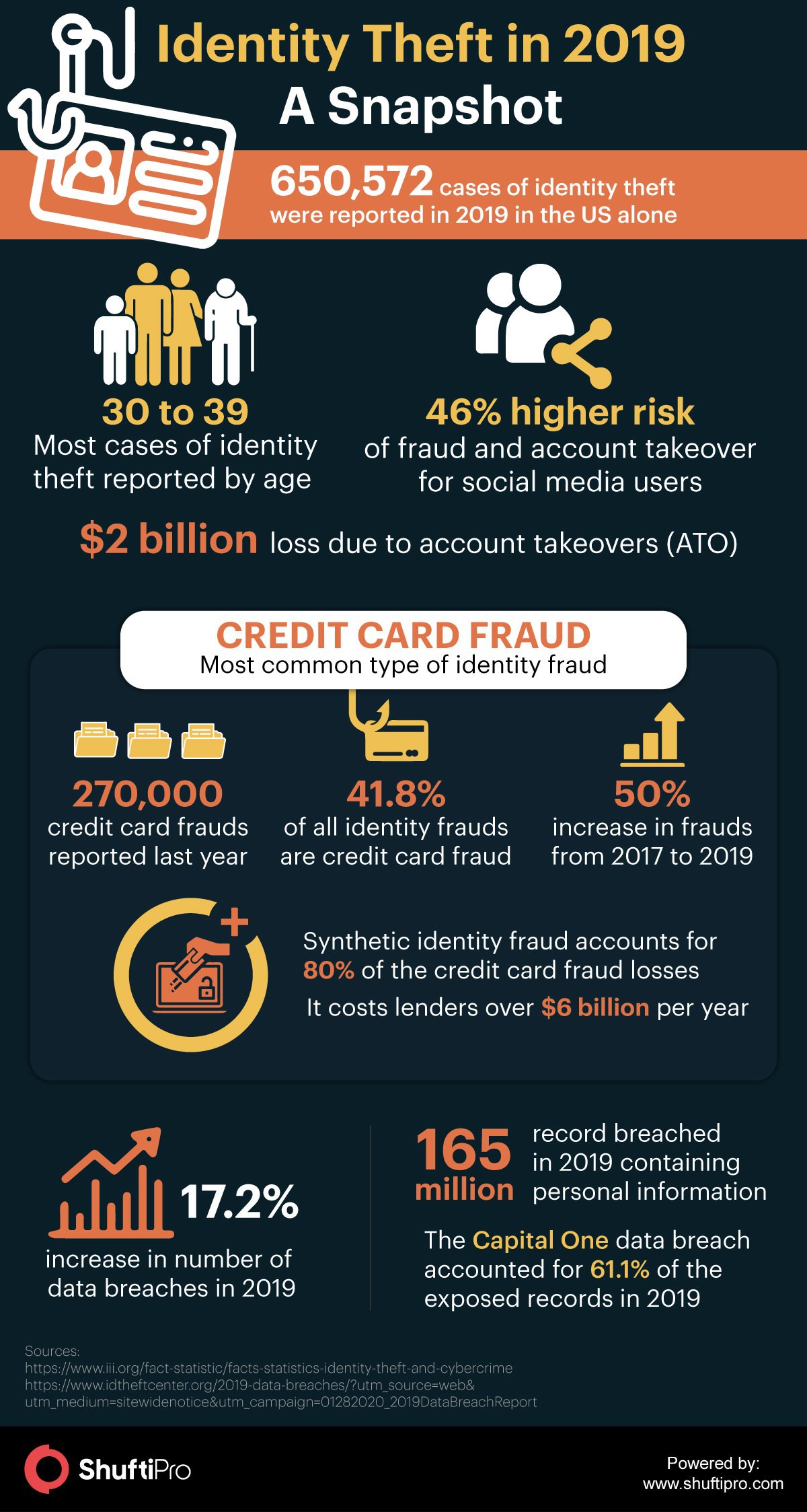
5 Types Of Identity Theft Fraud And How Businesses Can Prevent It




0 comments
Post a Comment